Looking More Closely at a Couple of Scam Emails
Like most people, I get lots of scam and phishing emails. They’re getting more sophisticated and personalized, which makes them even more dangerous, but there are still enough clues to alert you before you try to answer the email or click on the link. I’ve copied two of them to show some of those clues. The first one is less sophisticated and easier to identify as spam: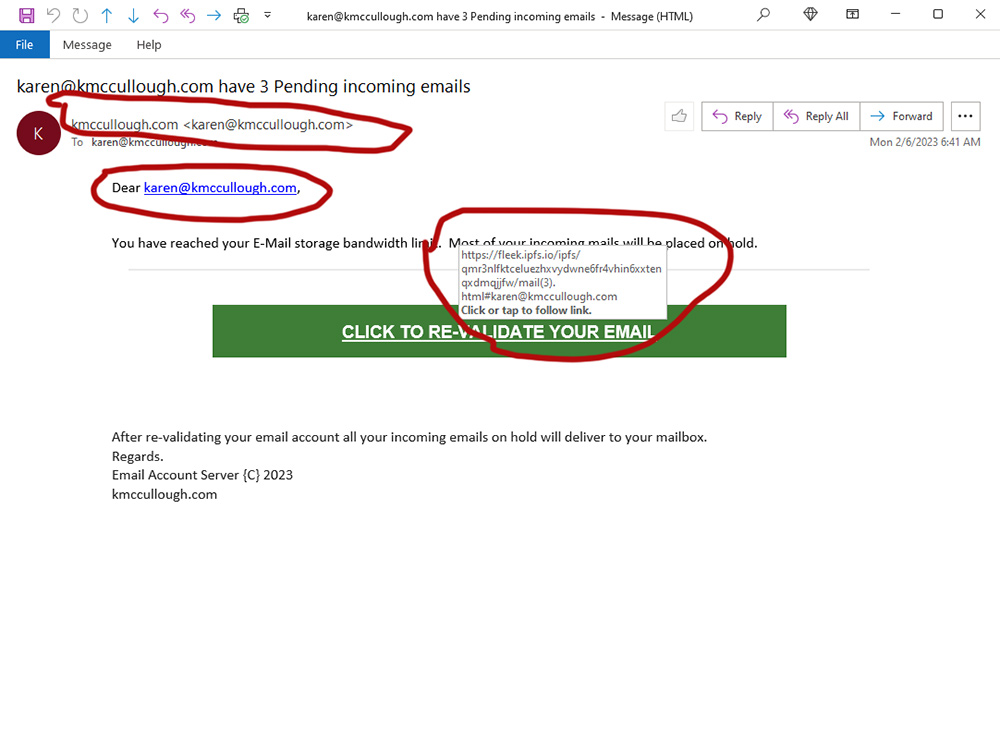
Clues:
- There is no company identification on this one at all; any legitimate message about email issues will include the name and usually the logo of the email host.
- The “from” address is my own email address; it should be from the email host service. (Note: “From” addresses are ridiculously easy to fake, so don’t let one that looks legit fool you into thinking the rest of the message is.)
- The message is addressed to my email address rather than to me by name. My email service knows my name and would address any legitimate email messages to me personally.
- The big one: When I mouse-over the green box, the actual link pops up as you see here. It doesn’t look anything like an address for my actual email server. Always pay particular attention to what is between the “https://” and the first dot because that’s the base server the link is sending you to. In this case, it looks like “fleek.ipso.io”. That bears no resemblance to my email host service address, which look more like “email.hostservice.com”. I’m using “hostservice as a placeholder, even though the next one actually does show the name of my email host service.
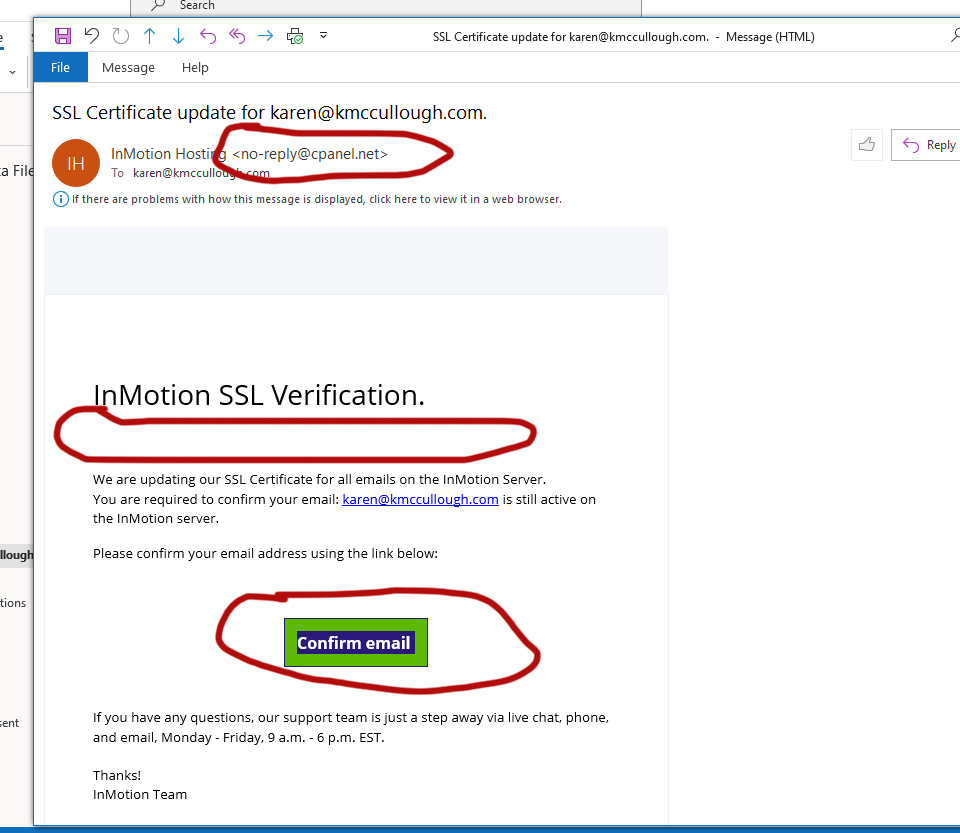
This one is a bit more clever:
- It does include the name of my hosting service, InMotion Hosting in the “From” line, but the actual email address shows cpanel.net, not inmotionhosting.xxx.
- Once again, the email is not addressed to me personally. They know my name and legitimate emails from them include it.
- The email uses “InMotion” but the company name is “InMotion Hosting, Inc.” and always identifies itself that way.
- This is a bit more technical, but the message about updating the SSL certificate for email is a bit of gobbledegook that sounds legit but in fact is nonsense.
- The final test. Unfortunately, I couldn’t get a screen grab that included the link that showed when I moused over the green box. But this is it: “https:// opwer90adfjepaawliapjerio.sdlficvuammosir. dweb. com / #karen@kmccullough.com” (I’ve added a few spaces to ensure the link doesn’t activate.)
I think these are both credential-stealing attempts. Clicking on the links would likely take me to a page that looked legitimate and asked me to sign into my email account with my user name and password. That would give them complete access to my email server. Alternatively, the link could take me to a page loaded with malware that would try to download to my computer. Both are actually possible as well. I’m not about to click on those links to see what would happen.
Note: I haven’t blacked out the name of my hosting service because it’s also very easy for anyone to find out with just a tiny bit of effort.
Bottom Line: Examine carefully ANY email that asks you to click on a link. Always mouse-over the link area and look closely and carefully at the actual destination.

 Clues:
Clues: